A Final year project on “Secret Communication System Using Multi-Image Steganography For Military Application” was submitted by Pratik Bhagwandas Wani (from JSPM’S Rajarshi Shahu College Of Engineering) to extrudesign.com.

Abstract
Information security plays an important role when considering data transmission. Generally, we use cryptography for information hiding and sending secret messages in the form of text. Nowadays, there are several techniques used for hiding information in any medium. One such technique is steganography. Building a secret communication system including Multi-image steganography will result in secure communication between the sender and the receiver without any interference from the hackers. Image steganography is the main aspect of information hiding where the ciphertext is embedded into an image called a cover image which is next to impossible for the intruders to see with their naked eyes. The hiding information can be any form of text, images, audio, and even videos inside a cover image. The conceptual definition of Multi-image Steganography is that the secret code is divided into multiple parts and is etched into multiple cover images. So we proposed two image steganography ideas to make it very challenging for the hackers to conceal the data. This survey paper proposes the Least significant bit(LSB) technique of Steganography and the Advanced Encryption Standard(AES) technique of Cryptography to build a safe and secure system. Here the sender and the receiver use the same key to encrypt and decrypt the data which is popularly termed a symmetric key. Also, a table summarizing all the details of these methods is included for better understanding/convenience.
Keywords: Multi-Image Steganography, Cryptography, Least Significant Bit LSB Steganography, Advanced Encryption Standard AES Cryptography, Information Hiding.
I. Introduction
Today communication systems have been digitally transferred to secure data transfer over networks. Information security is really important for a variety of purposes, especially in confidential data transfer, digital content access control systems for digital content distribution, data retention, and data protection from hackers. In particular, the security of information is divided into two parts namely encryption and cryptography.
Encryption is a popular and important algorithm that is widely accepted with regard to information security. Encryption consists of two key techniques: steganography and watermarking techniques. In our project, we will be using the concept of steganography which is used to hide data. The word steganography is derived from two Greek words: Stefanos means to cover and graphics means to write and usually refers to secret writing or data encryption. In this project, we use it to provide security and privacy. The content used to hide the data is called the cover object, and the cover and the hidden data are called the stego object. The techniques of steganography are divided into five: image steganography, video steganography, network steganography, text steganography, and audio steganography.
Types of Steganography:
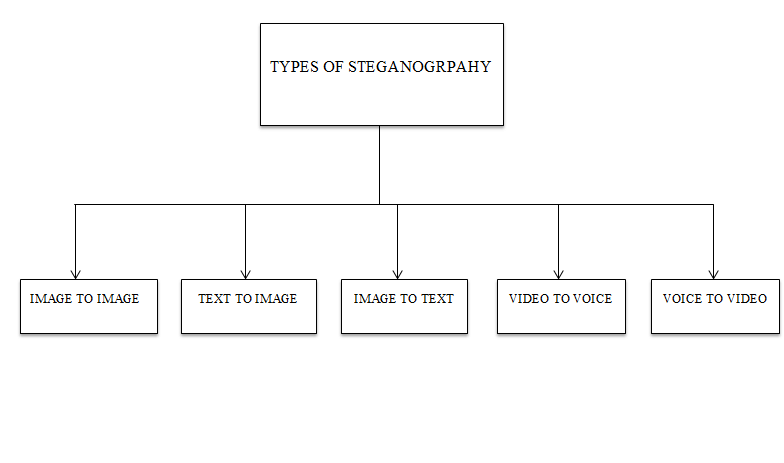
Our system uses text to image steganography.
Text to image – Here, the ciphertext is hidden under the image with the help of an asymmetric key.
With the help of LSB Steganography and the AES Algorithm Technique, we can use high-level information security without covering image damage. Least Significant Bit (LSB) is a system in which the last part of each pixel is adjusted and replaced by a bit of private message data. The AES has built-in flexibility within the main length, which allows for a level of “future assurance” against the progress of the ability to perform critical key searches. For example, it is 128 bits long, That is, AES works on 128 bits of blank text to produce 128 bits of ciphertext.
II. Highlights:
Below we have provided some important findings we came across while doing a literature survey for our corresponding system proposed in this paper.
[1] Paper: Image Steganography: A Review of Recent Advances.
Author: Nandini Subramaniam Omar Elharu
Year and Publication: 2020, IEEE
Description: Any form of internet connection with other network applications must be protected due to their increasing use. In this work, many security algorithms have been implemented and used to date. Until now cryptography has been a pillar of protection for secure data transfers. With the growing threat, Steganography has also replaced space for security. In cryptography, we change the natural way of data by using different security algorithms, which leads to increased security of the communication process. In Steganography, information is kept confidential to the attacker in order to securely transmit information through the use of images, audio, video etc.
[2] Paper: Secure Data Transfer Using Image Steganography
Author: Dakhz Mustafa, Abdulla, Siddeeq
Year and Publication: 2020, IJRCS
Description: The security of confidential information can be protected through cryptography or steganography. Steganography refers to the practice of encrypting a message (without tracing) in a way that does not make sense to anyone other than the intended recipient, while cryptography, on the other hand, refers to the art of converting a blank text (message) into an unreadable format.
[3] Paper: Hiding Data Using Efficient Combination of RSA Cryptography, and Compression Steganography Techniques
Author: Osama Fouad Abdel Wahab, Ashraf A. M. Khalaf, Aziza I. Hussein, and Hesham F. A. Hamed.
Year and Publication: 2021, IEEE
Description: Secret messages can be sent in private in the form of images or text so that no one other than the sender and receiver can read or see the message. Encryption and non-encryption of data that exist are known as steganography. In steganography, a picture that hides data is known as Cover Image because it covers a private message and after hiding the image data is known as a stego-image. In Steganography the inclusion of LSB is excellent and the most popular and widely used method of embedding data in the cover file. The LSB embedding method suggests that data can be encrypted in such a way that even the naked eye cannot identify hidden information in LSBs cover files. It is a local domain method. Cryptography is a method that converts text into codes for a hacker successfully receive a private message that cannot be read is a participant.
[4] Paper: Secure Mechanism For Communication Using Image Steganography
Author: Sakshi Audhi, Maruska Mascarenhas
Year and Publication: 2019, ICICICT
Description: Steganography is a data encryption method that aims to encrypt the data in such a way that an attacker cannot see the changes in the original media. Image steganography is more common and widely used compared to other forms of steganography. The Least Significant bit (LSB) is one of the most common techniques in steganography. The old method is LSB conversion. The main idea of this process is to directly change the specific LSB of the cover image with private data. An important drawback of the available LSB techniques is that increasing the capacity of the stego image leads to a reduction in its quality. Therefore, the goal of the proposed method to improve capacity is to consider the maximum visual quality.
III. Materials and Methods:
1. Cryptography
Cryptography can be defined as the process of protecting information and communication by using and compiling and deciphering coded messages, this can be proved in cases where communication is established between the two parties through an unsecured method that can easily be listened to by third parties or outside the public. Cryptography contains a collection of encryption techniques that include encryption and frameworks for encryption, integrity, digital signing, data privacy protection, and confidential transactions or communications. In this paper we will talk about different data encryption techniques; especially methodology that uses public-key cryptography, i.e. DES and AES.
1.1 DES (Data Encryption Standard):
The DES algorithm was created by the National Institute of Standards and Technology (NIST) in the early 1970s. Since it is a symmetric key algorithm, it uses the same key for both encryption and decryption of data. This process takes blank text from 64-bit blocks and converts them to ciphertext using 48-bit keys. Although it was a popular encryption algorithm in the ’90s, it was replaced by the AES in terms of modern computer computing power. Encryption strength is related to key size, and this is why DES found itself a victim of further technological advances in computing. After that, it was easy to remove DES encryption as 56-bit was no longer good enough to handle new technological advances and that is why it faced new challenges of being at risk of secrecy attacks.
1.2 AES (Advanced Encryption Standard):
It is necessary to replace DES as its key size is very small. With the growth of computer power, it is considered a threat to the full attack of search keys. DES triples were designed to overcome this problem but were found to be slow. This is where AES starts to shine, which is found to be 6x times faster than Triple-DES. The most popular and widely accepted algorithm for symmetric encryption that can be accomplished today is the Advanced Encryption Standard (AES). Unlike DES, in AES the number of cycles varies and depends on the key length. AES works on using 128-bit keys, 192-bit keys, and 256-bit keys having 10,12 and 14 rounds respectively. In Modern cryptography, AES is widely accepted and supported on both hardware and software. To date, no effective crypto-analytic attacks against AES have been detected. Additionally, AES has an inherently flexible key length, allowing a level of ‘future assurance’ against the advancement of the ability to perform key searches. It has been 20 years since the launch of the AES but still has not adopted any known. attack right now, which is why it can safely be called the unbreakable global standard of encryption. For these reasons, we will use AES in our proposed system approach.
2. Steganography
Steganography is the technique for hiding data and aims to hide data in such a way that any eavesdropper cannot observe any changes in the original media. Steganography is a data encryption method that aims to encrypt the data in such a way that any listener can see the changes in the original media. This is usually related to the way of hiding the existence of contact data. It hides information facts. It is a process of hiding data from one digital media to another digital media and retrieving the same information afterwards.
In our proposed approach we will be using LSB-based image steganography which is known as one of the most well-known techniques used for steganography. And in addition to today’s most popular method, steganography is the use of LSB image pixel data. This investigation is used for a single piece of LSB. It includes each piece of dual content and one piece of all pixels in the original image. This strategy works if the record is longer than the text message and if the image is grey, when the LSB technique is applied to all 24-bit image bits, three bits can be encoded in each pixel. Example: We can use images to hide. Things if we replace the last part of all the coloured bytes from the message.[1]
Image with 3 pixel

Fig. 2 Message A before encryption
Now we hide our message in the image.
Message A- 01000001
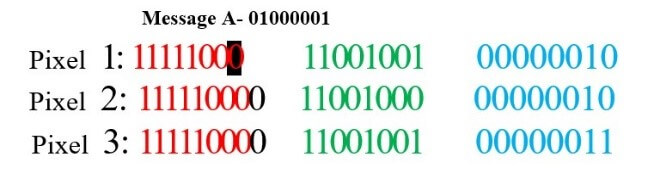
Fig. 3 Message A after encryption
3.1 Existing System
Every user wants to secure their data and personal information from hackers and any other harmful attacks. The transmission of data from the source environment to the destination environment should take place in a secure manner. For secure transmission of data, there occurs a crucial need for a special technique called Cryptography. Cryptography is one of the popular ways of sending critical information in a secret way. It hides the existence of the message. Cryptography includes the following important terms:
Plain Text-
It is the original message or text on the sender’s side.
Cipher Text –
It is the encoded message or text of the main message or text.
Encryption or Enciphering-
The process of converting clear text to encrypted text is known as Encryption.
Decryption –
The method of changing a secret message back into the ordinary readable form of the message is known as Decryption
The main disadvantage of cryptography is that the original text can be known and the cypher text is visible but we can’t read it although it can be decoded by the attacker. So, security is at risk. That is why to increase the security and improve the transmission of data we propose a system where along with cryptography, steganography is also used.
3.2. Proposed System
In this system, the User gives secret data as input. After receiving secret data system will encrypt secret data and divide cypher text into two parts. After that two cypher text embedded with cover images, i.e take from user /apply default images and create stego images for respective cypher text. Then send that images to the receiver. At the receiver end, the user will unite the stego images. after undergoing images decrypt the cypher text and merge plain text. We get secret data and then display the secret data.
– In LSB Steganography, hidden information is stored somewhere in the LSB image
– Take the binary representation of the hidden information and overwrite the LSB of each byte within the cover image
– Formula: cover image + secret key + hidden message = stego image
– Improved LSB method for hiding secret information written in a text file into colour images.
– Each character of the secret image is converted into its equivalent ASCII value and then each code is converted into an 8-bit binary, and each bit is inserted into the last LSB of each pixel of the cover image.
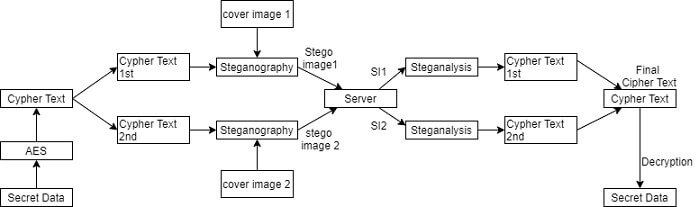
The system proposes an Advanced Encryption Standard (AES) algorithm for encryption of text as well as images and LSB i.e. least significant bit steganography approach for masking the data onto an image after encryption of the data.
In the first step, the Sender types the secret message to be sent and that secret message is encrypted using the AES encryption algorithm. If the sender sends an audio message then that message will convert from speech to text using Google API and secrete key will be generated. Further, the enciphered text message is embedded on to cover image using the LSB steganography technique. And then both the stego images are enciphered using an AES algorithm and a secret key.
Now the exact reverse of all the steps is performed at the receiver’s side.
First, at the receiver’s side, extraction of the enciphered images from the stego images is performed. Then the two stego images are decrypted using the AES algorithm by using the same key that was used to encrypt those two cover images on the sender’s side. At receiving end, we extract cypher text from stego images. And if the sender has sent the audio information then again we will convert that cypher text into the audio message using google API. Then the data embedded in the cover image is extracted. Finally, the data is decrypted using the same key which was used to encrypt the data in the initial module at the sender’s side.
The Flow of the System is:
- Take secret data/ message.
- Encrypt the secret data and divide the ciphertext.
- Embedded ciphertext with cover images and create stego images.
- Send stego-images.
- Unsteg the stego-images.
- Decrypt the ciphertext and merge the plain text.
- Get secret data.
- Display secret data/message.
VII. Result:
A system with three-layer security will be developed to produce a very safe approach by merging image steganography with cryptography which will hide the text for secret communication. This system will be very difficult to hack, and nobody can detect secret communication between military personnel. This will provide an end-to-end encrypted communication system.
VII. Conclusion
In summary, this paper has elaborated various techniques for information hiding used in recent times mainly Image steganography using the LSB algorithm and also for the encryption of the text we described AES cryptography which will divide the ciphertext into two which further gets embedded into two image files that are two stego image. We also proposed the steganalysis concept which is the study of detecting messages hidden using steganography; this is analogous to cryptanalysis applied to cryptography. The main approach to building this system is to provide strong security which will avoid detection of the data mainly when the hacker is desperate to decrypt the information.
Project Credit: This project “Secret Communication System Using Multi-Image Steganography For Military Application” was completed by Pratik Wani, Anuja Nanaware, Sneha Shirode and Aishwarya Suram under the esteemed guidance of Prof. Archana Jadhav of Department of Information Technology, JSPM’S Rajarshi Shahu College Of Engineering, Tathawade, Pune.
VIII. References
[1]IJSTR VOL-8, ISSUE 12, DECEMBER 2019: Image Steganography Using LSB by Dr. Amarendra K, Venkata Naresh Mandala, B.Chetan Gupta, G.Geetha Sudheshna, V.Venkata Anusha.
[2] Prateek Kumar Singh, Pratikshit Tripathi, Rohit Kumar, Deepak Kumar, IRJET, Secure Data Transmission, Volume: 04 Issue: 04 | Apr-2017.
[3] Dalia Nashat and Loay Mamdouh, An efficient steganographic technique for hiding data.
[4] Mustafa Sabah Taha, Mohd Shafry Mohd Rahim, Sameer Abdul Sattar left, Mohammed Mahdi Hashim, Hassanain Mahdi Alzuabidi, Combination of Steganography and Cryptography: A short Survey, ICSET 2019
[5] Ingemar J. Cox, Matthew L. Miller, Je_rey A. Bloom, Jessica Fridrich, Ton Kalker,” Digital Watermarking and Steganography”
[6] Hussein L. Hussein, Ahmed A. Abbass, Sinan A. Naji, Salam Al-rugby and Jasim H. Lafta, Hiding text in a grey image using mapping technique, IOP Publishing 2018

Leave a Reply