A final year project on “Design of Virtual Private Network (VPN) and Security Service″ submitted by Usman Shabbir to extrudesign.com.

Executive Summary
The focus of this documentation is the design of the Virtual Private Network and the Security Services to be implemented in the organization. The design is carried out on the basis of the requirement analysis, specifying the main features of the network deployed. We also emphasize the whole system’s architecture, screenshots have also been provided and ER diagrams are drawn using lucid chart.
Topic: Design of Virtual Private Network, establishing new VPN, Virtual private network
Introduction
With the increasing trend of up-to – the-minute communication, each organization has become mandatory to install an effective, safe and powerful network infrastructure. Networks frequently face assaults to crack data and disrupt rival activities.
In order to avoid one’s network, businesses implement virtual private networks to decrease the danger of external assaults, and to maintain data only in the network created and to improve effectiveness. We have been approached by XYZ Company to build a network for them so they can promote learners, facility and administrative employees, the organization needs an effective network infrastructure to process inner and external communication.
As we already have given them our Requirement Analysis Document which is approved by our Supervisor and our client, so now we are taking our self to the next stage of this project which is “Design Phase” and here we will design the network according to our final planning and updates.
Purpose and audience for the Design of Virtual Private Network
This document will highlight network Design including network specifications and implementations composed of network system architecture, network solutions with their topologies, IP Addressing tables with given Vlans for their respective sites, safety characteristics with inbound and outbound table, updated Redundancy plan and deployment plan, Configurations for our policies and future planning. Providing these guidelines, it will help the organization to make:
- Estimates of the bill
- Duration of implementation of each network stage
- Estimate network effectiveness, safety and performance
- In terms of network development and safety difficulties, the future of the installed network.
And here our audience you will find to be a company who we are working for: the “XYZ Company”.
Hardware and Software Requirements for Design of Virtual Private Network
| Item | Specifications |
| File Server | Cisco UCS S3260 Storage Server is recommended as file server as it is can be easily integrated with router and is efficient enough to handle data smoothly [1]To store data of the companyDrive bays support hot swapping to minimize downtimeDual two-socket server nodes based on Intel® Xeon® Scalable processors or Intel E5-2600 v4 CPUs with up to 44 cores per server node [1]Up to 1.5 TB of DDR4 memory per server node (3 TB total)Support for high performance NVMe and Flash Memory [1] |
| Application Server | Will help accessing the servicesWindows 2012 Server will be used as an application server because of its good reputation and versatility will be integrated to act as[1] |
| Router | Cisco 4000 Series Integrated Services Router is preferred for this security, supports virtualization, prevents from DDOS attacks, currently implemented, tested and recommended by professionals due to its efficiency and performance [3]. |
| Switches | Switch is used to distribute network from router to every device connected on the network.In the current network 8, 16 and 24 ports switch will be required.Cisco Catalyst 2960-L, model no. WS-C2960L can be used which is also available in 8, 16 and 24 port as WS-C2960-16TS and WS-C2960-24TS [4]. |
Other Requirements

| Firewall | Cisco Firepower Next-Generation Firewall can be considered as perfect option to detect attacks, stop threats, and make response. Plus, it is easily configurable [2]. |
| Cabling | Cables will be used across the LAN and to supply Ethernet connectivity to access points.For this purpose, CAT 6/6a Ethernet Cable will be used for distances below 300 feet’s and for the distance larger than 300 feet Single Mode OFC Cable will be used [5]. |
Abstract
This document will outline the design between the two sites of a secure network. In this research, a VPN – Virtual Private Network will be established for the organization. The organization has two Australian sites and its network should enable VPN access to the company’s remote clients.
Assumptions
Handing over this document will result in:
- The logical design will help vendors to choose the right type of hardware resources for the installation of network.
- Budget of the whole project will become predictable.
- Time duration for each milestone can be chalked out.
Design Strategy
Design strategy for the Design of Virtual Private Network should be strong enough to keep up good performance of the network under efficient security parameters.
- Strict authentication and verification for accessing the network.
- Encryption/Decryption of information.
- Access Control List and Firewall implementation.
- High restriction to server’s management.
- Backup plans
- Maintenance plan
- Reaction to DDOS attack and threats
- Minimalist Server downtime
Methodology
Virtual private networks that help people to remain anonymous on public connections by acting as a proxy server use the following methods for data security and safety.
1.1 IPsec
Internet safety protocol (IPsec) is a protocol that offers secure Internet network layer link. It was implemented to secure information transmission through a network by the Internet Engineering Task Force. IPsec design is consistent with authentication, integrity and confidentiality safety objectives. The data is encrypted in this security protocol, encapsulated in an IPsec packet, and the original IP packet decryption takes place at the end of the tunnel point when the intended user is DE encapsulated.
1.2 Layer 2 Tunneling Protocol (L2TP)
This security protocol is used together with the point-to-point protocol of Microsoft and Cisco. This protocol of safety can help to transfer non-IP protocol to an IP network. Due to the lack of confidentiality of L2TP, it is most commonly used in combination with IPsec. The IPsec system will appear as a single encrypted packet when all L2TP information is operating.
1.3 VPN link(S) between both sides
The Virtual Private Network between the two campuses will be built. The VPN will allow both ends to safely transfer information and use services. L2TP – Layer 2 Tunnelling Protocol is mounted to allow the link of both locations. The L2TP is solely liable for initiating the link, but no safety checks are carried out.
So in order to make the network more secure IPSec – Internet Protocol Security will be mounted with L2TP to make security parameters effective. IPSec offers a comprehensive encryption function for every information packet that is transmitted over the network. This is performed in 4 steps:
- Configure L2TP to connect both L2TP connections
- Create IKE Phase 1 Policy
- Configuring IPSec Policy
- Create crypto maps
These are the four steps involved in configuring a proper L2TP tunnel along with IPSec protocol [6].
VPN Architecture Diagram
The entire architecture is split into subsystem and is described in this segment.
1.1 VPN Architecture Diagram using Wireless Controller
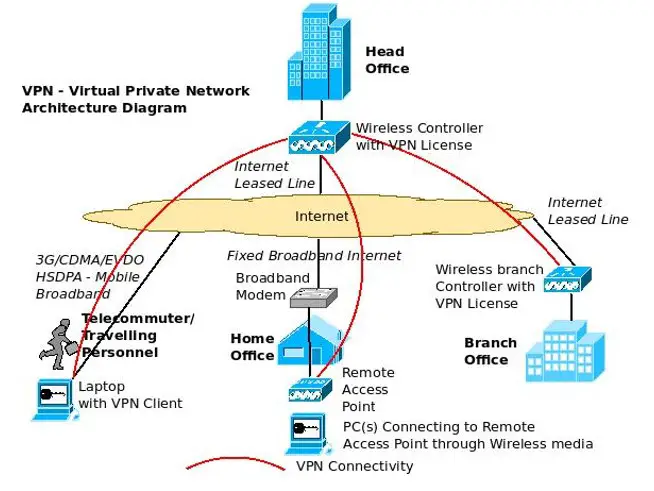
Here, the wireless controller of a company (used for centralized management of the various wireless access points of the company) can function as a VPN concentrator (with appropriate permits) and, if necessary, set up VPN tunnels with other controllers, remote access points (home office) and VPN clients (telecommuters / traveling personnel).
As shown in the above diagrams, it is not always necessary to have VPN links from headquarters to branch offices / traveling employees, etc. It can be created from one site to another, one site to multiple locations and multiple sites to multiple locations depending on the setup, designs and link types backed by the different VPN systems. Of course, both Site-to-Site and Site-to-Client VPNs can be set up.
1.2 VPN Policy Information Model
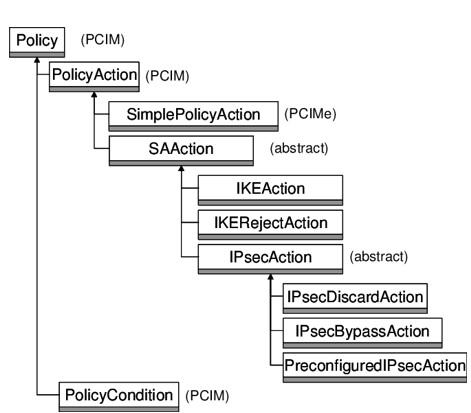
(A policy-based network management system for IP VPN – Scientific Figure on Techlivewire.com. Available from: http://www.techlivewire.com/figure/Hierarchy-of-VPN-Policy-Information-Model_fig1_224742035 [accessed 29 Aug, 2019])
Network Solution
1.1 Wide Area Network – WAN
The WAN between the organization’s two locations is as follows:
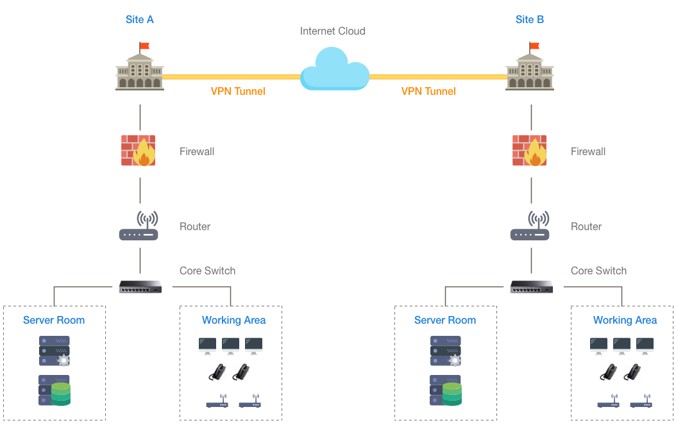
Between both locations, VPN tunnels will be introduced. One site will use Public IP to access the organization’s private IP and facilities to access the application server.
Note: Both locations may have server space, or the server may be accessible on one site only.
1.2 Local Area Network – LAN
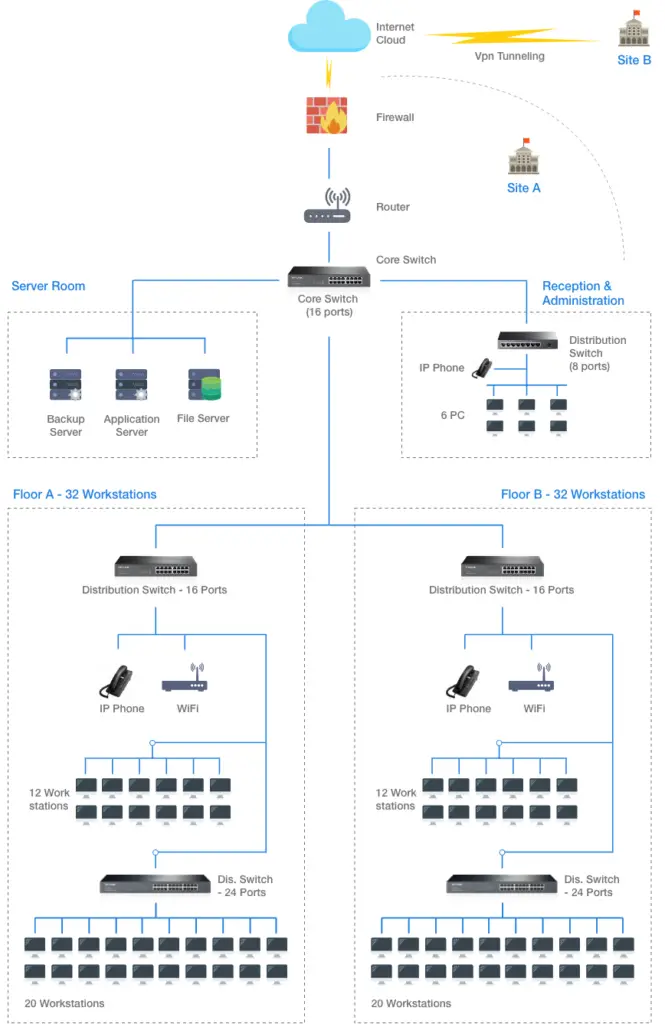
Note: the same design applies for site B
- The site’s LAN design is displayed above. Each organisation will use an ISP’s service to access the web for external interaction and use the intranet to communicate internally.
- Both sites will use VPN Tunnel to communicate services and access filer servers of applications or organisations.
- First, the firewall will be used to secure access, to respond to assaults and to scan viruses. The unauthorized users are filtered by ACL.
- The network will be transmitted via the core switch to the server area, administration and work area.
- The server space will have a data storage file server, a data backup server and a data processing software server. No DHCP server will be needed as installed modems will automatically assign IP addresses to the network devices.
- Area of reception may be regarded for the organisation where AP is accessible for IP telephone and some workstations.
- About 2 Floors can be regarded on each site. For users, 32 workstations, IP Phone and Wireless AP will be housed in each floor. Switches will be used for network distribution to these points of access.
IP Addressing and VLAN With Diagram
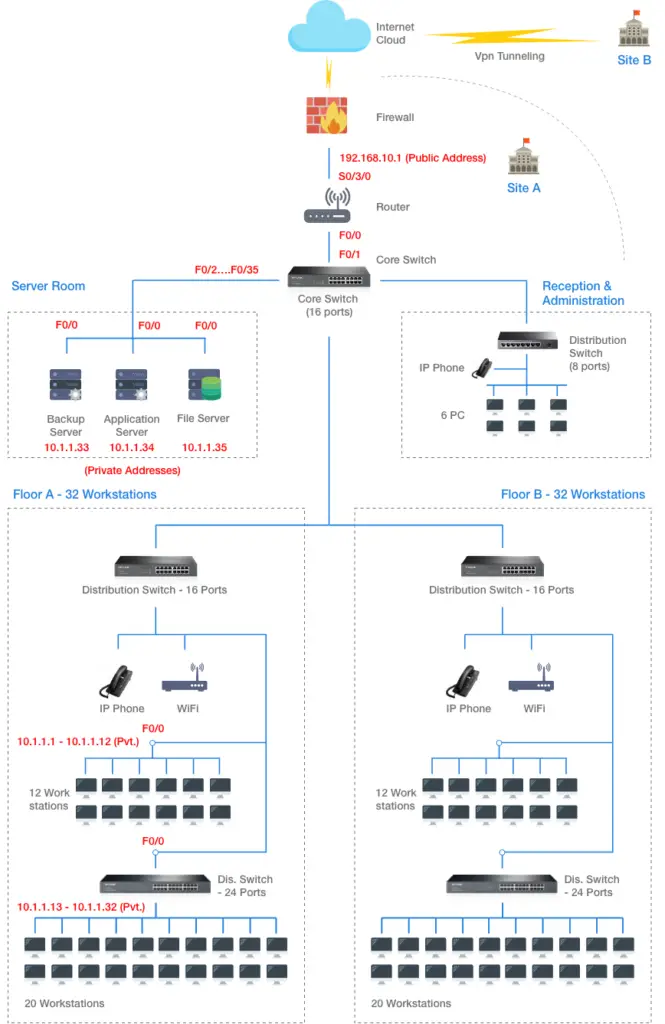
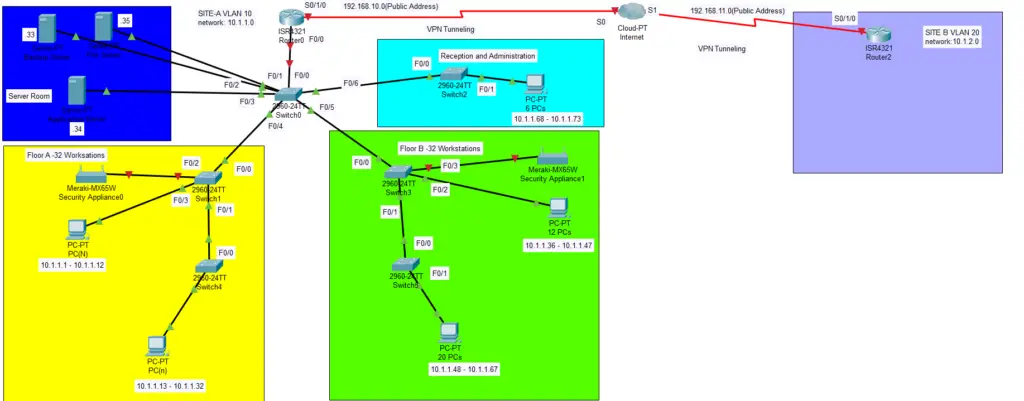
1.1 Logical Diagram of Data Flow-Through Packet Tracer
1.2 IP Addressing for Site A
VLAN 10
| DEVICE | INTERFACE | IP ADDRESS | SUBNET MASK |
| ROUTER 0 | F0/0 | 10.1.1.7 (PRIVATE) | 255.255.255.0 |
| S0/1/0 | 192.1.10.0 (PUBLIC) | 255.255.255.0 | |
| PC 0 | F0/0 | 10.1.1.1 (PRIVATE) | 255.255.255.0 |
| PC 1 | F0/0 | 10.1.1.2 (PRIVATE) | 255.255.255.0 |
| PC 2 | F0/0 | 10.1.1.3 (PRIVATE) | 255.255.255.0 |
| PC (N) | F0/0 | 10.1.1.(N) (PRIVATE) | 255.255.255.0 |
| SERVER 1 | F0/0 | 10.1.1.33 (PRIVATE) | 255.255.255.0 |
| SERVER 2 | F0/0 | 10.1.1.34 (PRIVATE) | 255.255.255.0 |
| SERVER 3 | F0/0 | 10.1.1.35 (PRIVATE) | 255.255.255.0 |
Table A – IP Addressing Scheme for SITE A (note: it is only representing for floor A and server room. For floor B and administration department will be the same as follows.)
1.3 IP Addressing for Site B
VLAN 20
| DEVICE | INTERFACE | IP ADDRESS | SUBNET MASK |
| ROUTER 2 | F0/0 | 10.1.2.7 (PRIVATE) | 255.255.255.0 |
| S0/1/0 | 192.1.11.0 (PUBLIC) | 255.255.255.0 | |
| PC 0 | F0/0 | 10.1.2.1 (PRIVATE) | 255.255.255.0 |
| PC 1 | F0/0 | 10.1.2.2 (PRIVATE) | 255.255.255.0 |
| PC 2 | F0/0 | 10.1.2.3 (PRIVATE) | 255.255.255.0 |
| PC (N) | F0/0 | 10.1.2.(N) | 255.255.255.0 |
The goal is to link two sites online. Private addressing system will be performed at each site in such a situation. In the present organisation, 10.1.1.0 is assigned to Site A and 10.1.2.0 to Site B.
Security Features and Policies
In order to make the network secure, the following design is prepared:
- Firewall will be installed to protect network from viruses, attacks and threats. Protocol filtering, inspection of packets will be performed by firewall. Firewall will also perform Policy enforcement.
- Kerberos Authentication will be performed for each user accessing the file server or application server.
- Session token will be granted to each user on the network which will expire after a specific interval of time.
- ACL – Access Control List will be prepared to manage inbound and outbound traffic.
| Inbound | ||||||
| Rule # | Type | Protocol | Port Range | Source | Allow/Deny | Comments |
| 120 | SSH | TCP | Can be for a specific port .i.e. 2409 | IP Addresses of both Sites | Allow | Allows inbound SSH traffic from both sites and from public address. |
| 130 | RDP | TCP | Can be for a specific port .i.e. 2449 | IP Addresses of Sites | Allow | Allows RDP inbound traffic to web servers from the public IPv4 address of the branch network. |
| * | All IPv4 traffic | All | All | 0.0.0.0/0 | Deny | All unhandled traffic will be denied. |
| Outbound | ||||||
| Rule # | Type | Protocol | Port Range | Destination | Allow/Deny | Comments |
| 100 | All IPv4 traffic | all | all | [Application Server’s IP Address] | Allow | Allows all the traffic to access Application Server and internet. |
| * | All IPv4 traffic | all | all | 0.0.0.0/0 | Deny | Denies the unhandled addresses to access the internet. |
- Implemented VPN will provide secure communication between both sites.
- By using IPsec, every data bit will be encrypted, hence making the network secure.
- ISAKMP will be implemented that will give privilege to routers on both end to decide a specific encryption method for the data [7].
- Authentication will be performed using pre-shared key between both ends.
High-Availability and Redundancy
High availability for the sites should be regarded a must. As the event may be, both the VPN systems and the firewalls should be configured in high-availability pairs. In the future, this can be expanded to all other locations to eliminate the single points of failure, but it is more critical at the hub locations, as an outage there would result in a disastrous loss of a big part of Company XYZ VPN traffic. It is possible to extend the subsequent design and debate to include this level of redundancy. Additional steps can be taken to guarantee that the VPN is available, such as using various redundant Internet links, as well as routing protocols, in order to further armour the system from network mistakes.
VPN service Deployment and implementation
The VPN allows only two ends to interact with each other, but it does not have a security parameter. The IPSec protocol suite will be used to conduct safety checks to authenticate the information. IPSec, the Internet’s main protocol, encrypts every data packet that is sent through the tunnel.
L2TP – Layer 2 Tunnelling Protocol and IPsec are paired to create a safe VPN connection. In this current network, at each site, L2TP will create and connect tunnels between L2TP points. Whereas IPSec will be accountable for encrypting the client-host information exchange as well as handling secure communication through this tunnel.
Configurations
The configuration of L2TP IPSec involves 4 steps.
1.1 Configuration of VPN Tunnel
Configure L2TP to connect both L2TP connections
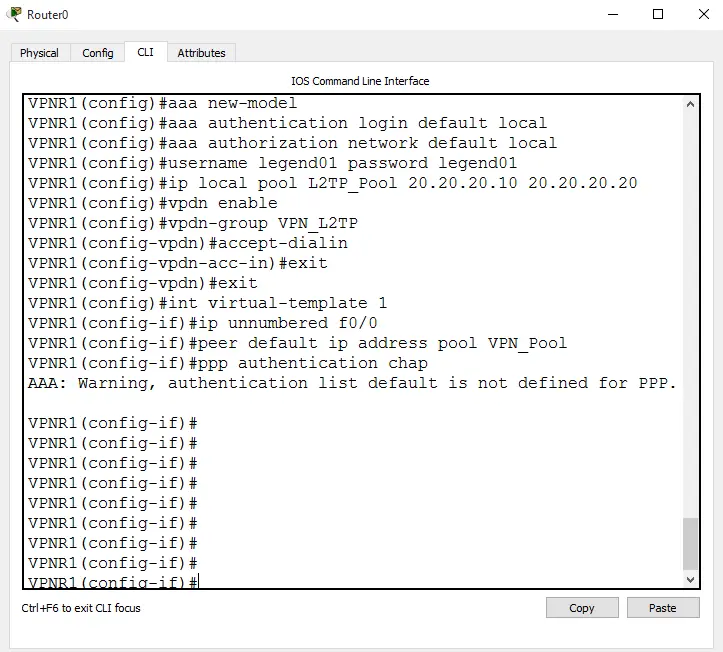
1.1.1 Configuration Steps
- To enable the access, authentication and accounting: aaa new-model > aaa authentication login default local > aaa authorization network default local
- To set username and password: username legend01 password legend01
- To set local pool for the VPN: ip local pool L2TP_Pool 20.20.20.10 20.20.20.20
- To Enable vpdn: vpdn enable
- To Set vpdn group: vpdn-group VPN_L2TP
- To accept dial-in: accept-dialin
- To set L2TP protocol: protocol l2tp
- In order to enable virtual: virtual-template 1
- In order to set no authentication for L2TP with the command: no l2tp tunnel authentication
- To configure interface virtual: int virtual-template 1 > ip unnumbered f0/0 > peer default ip address pool L2TP_Pool > ppp authentication chap
Note: a few commands are not included in the screenshot, as IOS Version does not support these.
1.2 Create IKE Phase 1 Policy
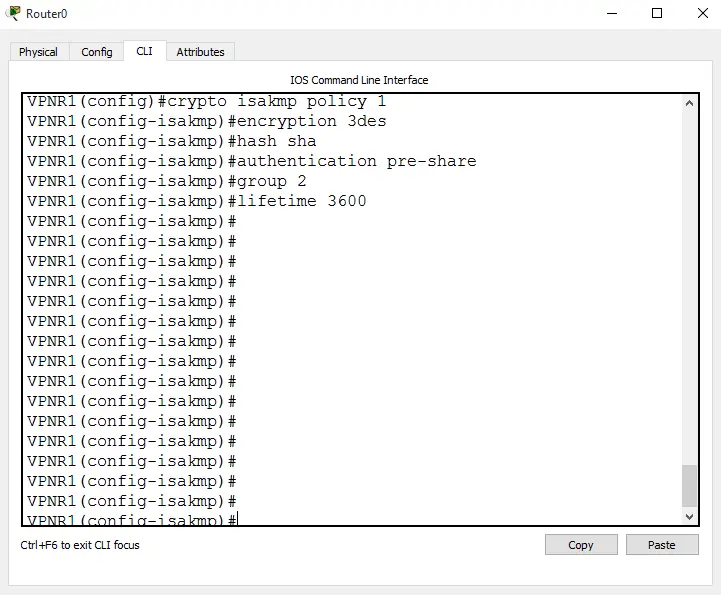
1.2.1 Steps for Configuration
- To configure ISAKMP Policy: crypto isakmp policy 1
- To set the security package encryption algorithm: encryption 3des
- To set the protective hash algorithm: hash sha
- Set technique of authentication for the security package: authentication pre-share
- To set the Diffie-Hellman group: group 2
- To set lifetime security association for ISAKMP: lifetime 3600
1.3 Configuring IPSec Policy
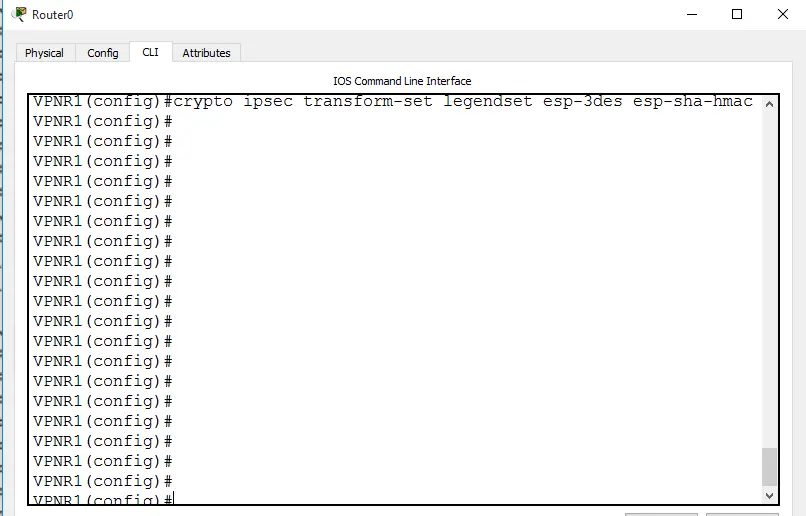
1.3.1 Configuration Steps
- To configure IPSec policy: crypto IPsec transform-set legendset esp-3des esp-sha-hmac
- To set IPSec mode: mode tunnel
Note: A few commands are not included in the screenshot, as IOS Version does not support these.
1.4 Create crypto maps
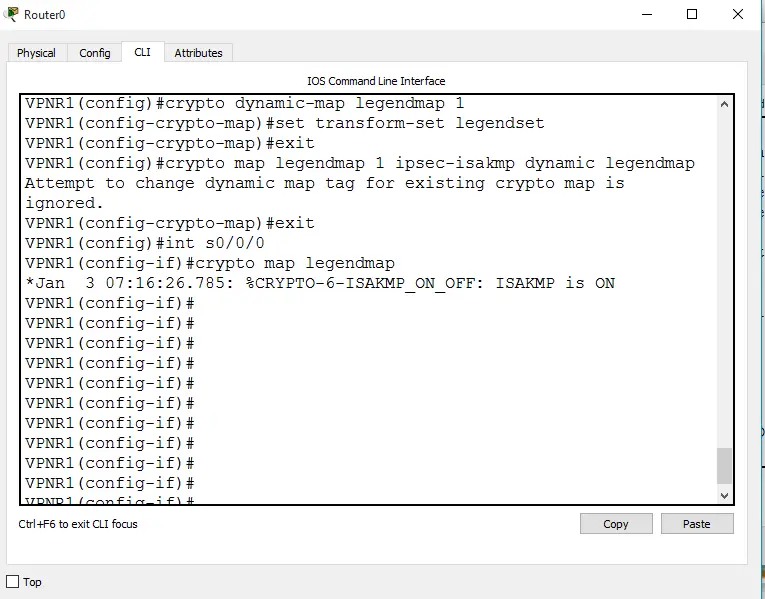
Figure 8 – Configuration for Crypto Maps
- To specify a dynamic crypto map template: crypto dynamic-map legendmap 1
- To set values for encryption/decryption: set transform-set legendset
- To enter a crypto map with the command crypto map legendmap 1 ipsec-isakmp dynamic legendmap
- To make an interface able to use crypto map: int s0/0/0 > crypto map legendmap
These are the four configuration steps involved to configure a proper L2TP tunnel along with IPSec protocol.
Future Planning in Design of Virtual Private Network
As we move into the development and testing stage, we plan to begin the development phase as quickly as possible. We will design the network in such a manner that all the tasks we mentioned previously can be fulfilled. In addition, by releasing fresh updates, we will retain our network to make it function even better
Conclusion
Virtual Private Network provides the organisation with several advantages as it helps to decrease costs as there is no need for a longer lease line, lowering the cost of assistance. It also solves the network’s scalability issue for global or remote places in particular. VPN enhances network security, by maintaining it encrypted, it protects information from hackers and intruders. In the nations where internet censorship is implemented, it also used to unblock websites and bypass filters. While using the web application or websites, VPN also offers internet anonymity.
References
- “Cisco UCS S3260 Storage Server”, Cisco, 2018. [Online]. Available: https://www.cisco.com/c/en/us/products/servers-unified-computing/ucs-s3260-storage-server/index.html. [Accessed: 26- Aug- 2019].
- “How Firewalls Work? | What Firewall Does Against Unknown Threats”, Comodo. [Online]. Available: https://www.comodo.com/resources/home/how-firewalls-work.php. [Accessed: 01- Sep- 2019].
- “Cisco 4000 Series Integrated Services Routers”. [Online]. Available: https://www.cisco.com/c/en/us/products/routers/4000-series-integrated-services-routers-isr/index.html#~stickynav=1. [Accessed: 26- Aug- 2019].
- Cisco. Cisco Catalyst 2960L-16TS-LL Switch. [online] Available at: https://www.cisco.com/c/en/us/support/switches/catalyst-2960l-16ts-ll- switch/model.html
- Datatechprofessionals.com. (n.d.). Cat5e vs Cat6 vs Cat6a vs Cat7 – Which type of cable should I use?. [online] Available at: http://www.datatechprofessionals.com/cabletypes.html. [Accessed: 02- Sep- 2019].
- “Configuring Layer 2 Tunneling Protocol (L2TP) over IPSec”, Cisco. [Online]. Available: https://www.cisco.com/c/en/us/support/docs/security-vpn/ipsec-negotiation-ike-protocols/14122-24.html. [Accessed: 2- Sep- 2019].
- R. Mupiun, “What’s the difference between IKE and ISAKMP?”, Network Engineering Stack Exchange, 2015. [Online]. Available: https://networkengineering.stackexchange.com/questions/1/whats-the-difference-between-ike-and-isakmp. [Accessed: 25- Aug- 2019].
Keywords: Design of Virtual Private Network, VPN, Virtual private network, data security, Security Services

Leave a Reply